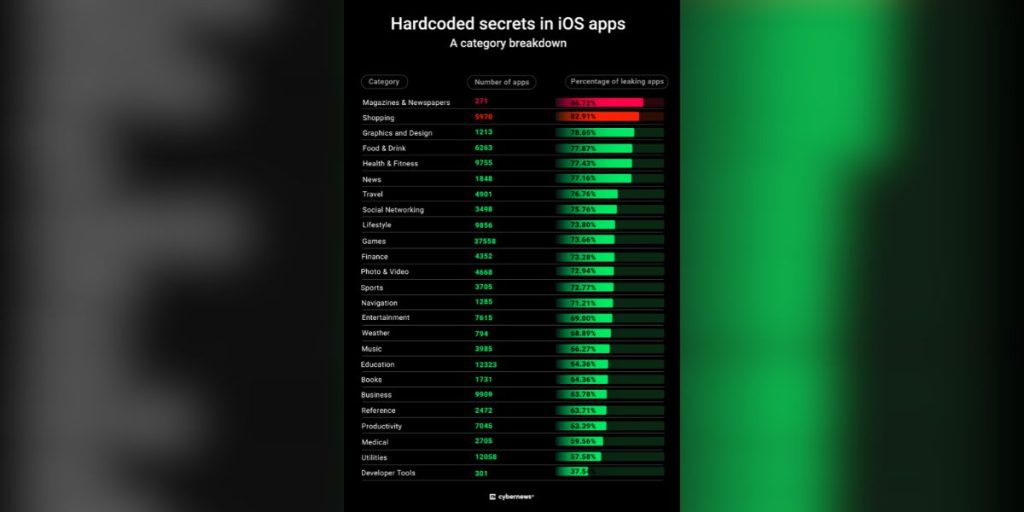
Cybernews researchers analyzed 156,080 randomly selected iOS apps—about 8% of the total available on the Apple App Store—and found that 71% leaked sensitive data, including API keys, cloud storage credentials, and financial information.
This research, one of the first large-scale studies of its kind, suggests that iOS apps remain vulnerable to cybersecurity leaks despite Apple’s strict evaluation guidelines.
Here is a summery of its report::
Over 816,000 secrets were found, with an average of 5.23 exposed secrets per app.
Out of 94,240 storage bucket instances found hardcoded in iOS applications (with some apps containing multiple storage bucket endpoints), 836 of these endpoints (0.89%) were accessible without authentication, exposing 406TB of user files, personal data, and documents.
If you were to stream HD video, 406TB would allow you to watch for approximately 17 years of non-stop HD content.
2,218 Firebase instances (4.34%) had misconfigured authentication, leaking 19.8 million records (33GB of data), including user session tokens and backend analytics, almost all of these instances hosted in the US.
This is the equivalent of 16 million photos from an iPhone.
More than 51,000 apps misuse Google’s Firebase database, making user data vulnerable to easy theft.
That’s more than the number of Starbucks locations worldwide – each one representing an app where sensitive data is at risk.
According to the Cybernews Research team, they selected extracted, and analyzed the code of 156,080 randomly selected iOS apps for hardcoded secrets. Apple claims that 1.8M apps are available in the App Store worldwide, meaning that the research covered around 8% of apps. The analyzed application versions were from October 2nd-16th, 2024.
The researchers didn’t attempt to de-obfuscate or de-compile the apps. Despite that, a staggering amount of secrets were found in plaintext files stored within the apps’ IPA archives, which can be easily extracted.
Cybernews also checked the cloud bucket and Firebase endpoints to see if they had authentication.
Cybernews researchers also said they extracted around 79,000 Google Project IDs, which are unique identifiers for Google Cloud Platform projects. These IDs are used to route API requests and manage resources. Apps need to include them when communicating with Google, which uses them for organization and billing.
A similar number (79,000), of Google App IDs was also discovered. These keys are used to identify apps displaying ads and track usage statistics. They’re meant to be integrated into the source code.
Watch this to see how this works:
Other most commonly leaked low-sensitivity secrets include almost 68,000 Client IDs, 43,000 Google AdMob Application IDs, 37,000 Facebook App IDs (which are used to interact with the platform’s services), 20,000 Android Client IDs, and almost 17,000 Facebook Client tokens.
The entire report is here: https://cybernews.com/security/ios-apps-leak-hardcoded-secrets-research/

